Today I realised I was totally vulnerable to a cyber-attack. As the head IT person within Bowhill Engineering, I thought I was better prepared.
My passwords can be hacked instantly… and one of the “work” passwords had been repeated 42 times!
I’m the one who reminds others within our company of the risks involved, but at a recent Cyber Security Event, put on jointly by AusIndsutry & RDAMR by the Cyber & Infrastructure Security Outreach team, I quickly realised how complacent I had become.
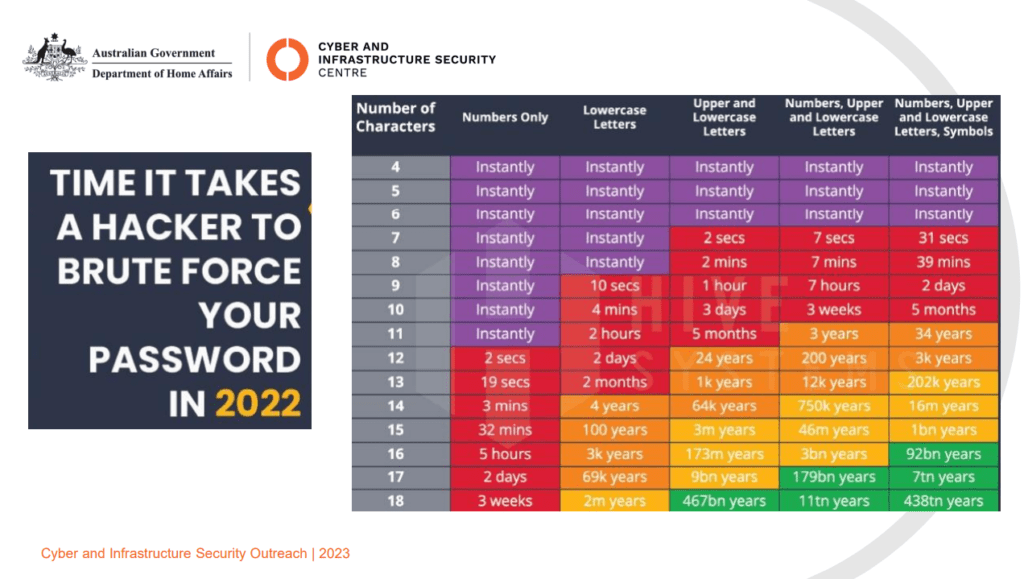
I prided myself in my password management – Numbers, Upper & Lowercase, Letters & Symbols, but looking at the chart, I quickly realised that this was no longer good enough.
My biggest realisation was around using the same password over & over – that although I was quite diligent in the complexity, I was still very vulnerable because if one of these sites are hacked, then all the other sites are vulnerable.
Cyber incidents are at $33 billion in Australia annually, an incident is reported every 7 minutes, 1 in 4 businesses have had an incident… and this figure is only for those that are reported, many people feel vulnerable and embarrassed to report, so the real number is most likely much higher. The average cost is $39k for a small business and $88k for a SME… who can afford that?
A huge takeaway for me was “awareness & education” over software upgrades is the key. Encouraging staff to be open & report any unusual incidents.
Ensuring all our staff passwords are unique for each site, length over complexity (refer to chart), this costs nothing (but a little time to implement). This one change will make a huge impact and if one site is breached, you can have confidence that this password can be changed and other sites won’t be impacted.
Another takeaway that should be quick and easy to implement was internal security permissions. The principal of least privilege, which will reduce the risk of spread if an incident occurs. How many of us have got lax with our internal security permissions, giving all staff full access, or access to areas that they don’t really need.
From this 2 hour workshop I’ve realised that I’m totally reliant upon our 3rd party IT provider to ensure we are “safe” – but not really knowing how or what to check. I’ve now gone out to tender to 3 other parties (for due diligence) and as I talk to other providers, I’m realising how complacent we’ve been and justassuming that everything is setup as thought is a huge risk. Are backups really working, have we had a practice restore? Are patches being installed & all workstations up to date? Are remote montoring systems on all workstations, or have some been missed? Is MFA enforced, or only enabled? What security policies apply to BYOD… and the list goes on.
Can you afford to be next? What are you going to do to help reduce the risk?













